Review Your Data Needs, Security Procedures

Business Record Staff Dec 29, 2017 | 2:00 pm
4 min read time
922 wordsBusiness Insights Blog, The Internet of ThingsBY DENNY FISHER, Chief strategist, ACS
It’s the time of year when many reflect upon the past and prepare for the future. Your organization’s network needs the same attention, whether it is an analysis of the data you collect and how it’s utilized, or an examination of your security strategy and whether everything is in place to stop an attack.
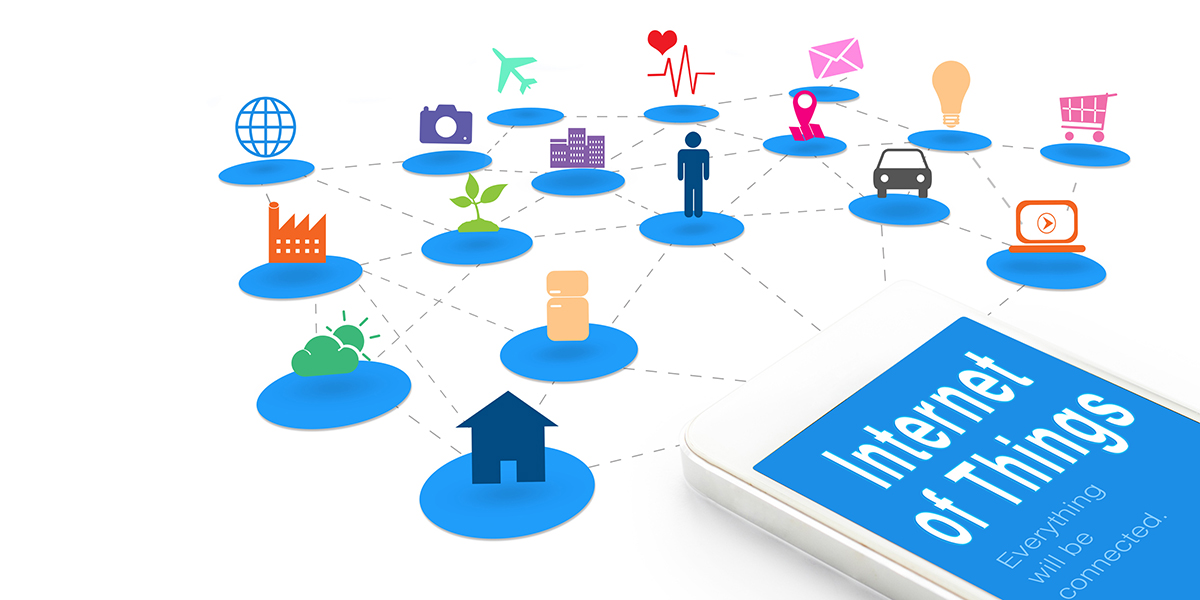
You use technology and the Internet each day in your business and personal life to make things run more efficiently. This is known as the “Internet of Things.” It includes everyday objects that are embedded with network connectivity, electronics, software or sensors that send and receive data. It’s important to understand how these devices work and how you can leverage them to your benefit.
The IoT is technology that can transform your business – you can use it to control your electricity consumption, monitor fuel usage, determine which products to place in which stores and so much more – but it’s imperative you know how to use it appropriately to securely mine the best data and to keep your other devices and network protected.
One of the biggest mistakes you can make is using wireless Internet and public networks with your IoT devices.
Hackers use public wireless networks to gain access into other users’ personal information and to install malware programs that damage or disable the device or system. The risk extends beyond the immediate use of your personal devices. If you connect into another network, say your company’s, your device can transmit malware and viruses into that system that were installed or that it picked up while connected to public wireless.
Any use of public wireless should be thoughtfully considered, and avoid connecting to any accounts that require a username and password. Applications that continuously run in the background such as Yahoo Mail or even your corporate email are vulnerable to hackers once connected to the public network.
All devices should have an antivirus and malware safeguard installed when possible, and businesses should have a layered security approach to defend themselves against and block outer edge risks.
A layered security approach will protect the entire business network and allow for multiple ways to authenticate a user and protect a business if its outer edge network is compromised. This includes an outer layer of a firewall, web and email security applications that block out spam, to the inner core, the data center layer, that protects the most important information.
All protective measures and IoT devices need to be incorporated into network security policies. All employees should be trained in these procedures, and at a minimum the procedures should be reviewed annually.
Now that you know how to secure these areas, you need to make sure you have a plan to store the influx of data you will receive through the IoT. You’ll want to determine which data are most important to your business, as well as how you’ll store and back up the data, depending upon how quickly or frequently you’ll need to access it in case of a network failure.
Better data lead to better decision-making when it comes to business. That’s why you’ll want a data analytics or business intelligence tool to help you sort through the millions of pieces of information that are collected through the IoT and analyze which are most critical.
It’s important to have a quality server to optimize your analytic tools and enable them to sort through your volumes of data. You’ll want one that is reliable and secure, has virtualization built into the hypervisor/firmware rather than being a software add-on, has the flexibility to fit your system and can support multi units of work at once or preschedule them for completion.
You know you have a lot of data; it needs to be secured and analyzed to help you make the smartest business decisions. The question is “How do I do all of this?” Because of the growing number of IoT devices connected to a network, some businesses haven’t taken the time to incorporate them into their business strategies.
A managed services provider can help you navigate through what to monitor and how to monitor it.
Part of monitoring your network will include an incident response plan. The plan will assist in managing business or personal data in case of a cyber threat, power outage or physical disaster that destroys or disables the systems that support your information. The plan will be part of the company’s overall Business Continuity or Disaster Recovery Plan.
You’ll also want to include your IoT devices in the plan by first conducting a business impact analysis to consider how valuable the data are for each device based on what information it produces and whether that information drives revenues or produces cost savings.
None of this can work without educating those involved. Ensure your employees understand the risk, know how to use their devices and take precautions to keep the company’s network safe, both while at work and while working remotely or from home.
You now have the foundation to utilize your IoT devices and have a edge over your competition. A third-party security assessment company can take you to that next step. A partner can evaluate a company’s procedures and policies to ensure all layers effectively work together, as well as guide the business to the right solutions to mitigate risk, reduce costs and increase revenue.
Reach any of our experts to learn more about the above topics or to answer any other security or network questions at contact@acsltd.com.
 |
Denny Fisher, Chief Strategist View Bio 515-223-0078 contact@acsltd.com acsltd.com/br |